Decentralized Identity – A look into Decentralized Identity (DID)
Mobile and Internet users willingly share their identification when they want to share the whereabouts and people they are accompanying. These credentials are of the personal information hence the control on access is necessary.
Presence of individuals tracked with their footprints on internet provides information on individual’s activities. The data collected, processed, segregated, and used to establish customer relations operates through decentralized identity.
With the change of our online experience, the way we interact with the world has changed. This digital transformation has touched the lives of individuals and altered business approach.
Various sites and every website or application we login or register, manages our online identity, such as e-commerce, shopping, telecom, finance. In case security of data, we have absolutely no control.
Decentralized identity empowers and enables the individual to protect and control their personal information. It eliminates the requirement for centralized authorities resulting in success of managing identifiers, verification keys, and service endpoints.
What exactly is a decentralized identity model?
UPI- Unified Payment Interface launched by the NPCI- National Payments Corporation of India is also a decentralized identity. It has changed the way payments made online. You can download the mobile app for UPI of respective bank that you often use or multiple banks. Create a profile by adding the personal details like name, address, bank account. There is no need to remember the login id and login/ transaction password. With mPIN, OTP, and the debt or credit card expiry details, it adds to the security. UPI saves time as there is no need to add payee. The VPS- Virtual Payment Address is must to transfer the money. You can transfer no matter whether that person has the account is same bank or not. You can pay for the utility bills, entertainment etc. There are no charges for UPI transfer and the limit of one lakh per transaction is that too safe. It is a proof that decentralized identity radically simplifies this process.
Decentralized Identity – Benefits to Individuals & Business Enterprises
- Self-owned Identity: The identification is decentralized making it password free access. It stores the proof of identifiers and they have right of controlling the digital identity.
- Greater Control of data: This proof based DID checks cryptographic proof while interacting with other entities. The coded seals need encryption thus keeps the data under control.
- Data Storage: The permissions granted to stored data make the safe to communicate. The stage of data authentication becomes one time activity unless user updates it.
- Greater privacy: The privacy of their information facilitates entities to select and control the level of disclosure, by selecting the attributes of data. The purpose of use is clearly available; hence, the privacy level can be of user’s choice.
- No central authority control: This is possible as entities discover DIDs for other entities. It gives individual and organizational entities, both the power to control their digital identifiers. There is no dependency on the external authorities.
- Improved security of applications: The dependability of the DID documents provides security to multiple parties. This required level of assurance, accredits the data, and helps in taking progressive actions towards the business activities. A DID document contains information that is cryptographically authenticated, which speeds up the process as well as services.
- Unique Identification: The difficulty level of identification has tremendously descended due to decentralized identity. The conservative identity management systems had centralized authorities for certification and domain name registries covering the procedurals of identification.
- Trustable interactions: Dealing with all requests for identity and access is possible once user proves identity to a trusted third party. The proof of identity is stored in its related infrastructure. Every interaction is pre- certified when it comes to third party dealings. The entities need not wait for the certifications as the authenticated data enables the transactions smooth and efficient.
- Data Exchange after Authentication: DID uses interoperable standards of infrastructure so that it can make use of existing software libraries and tools designed specifically for ease of operations.
- Portability: The system and network independent decentralized identity enables certain entities to use digital identifiers. DID supportive system have ability to introduce simplicity, extensibility, interoperability, and portability to the decentralized identity.
- Documentation of using DID: Decentralized Identifiers –DIDs make independent digital identities verifiable. DID Documents are simple documents that contain guidelines on using that particular DID. Every DID document should at least have purpose of proof, verification methods and the service endpoints. The proof purposes in combination with verification methods provide mechanisms for ascertaining things. DID document consist of defined verification method just as cryptographic public key created for the purpose of authentication and the service endpoints enable trusted interactions using the DID controller.
How does Decentralized Identity function?
With the changing technologies there is need to standardize things that helps in user identification. Identity verification innovatively brought the concept of user controlled datastores.
The user data is available in fragments across thousands of apps and services they avail.
- Decentralized Identifiers: DIDs has ID users that can own, and control identity independently. They are globally unique identifiers were developed in 1980’s and afterwards became the standard feature of open source. Linking of decentralized Public Key Infrastructure (DPKI) to DID is must. The JSON documents contain public key material, its authentication descriptors, and service endpoints.
UUID and DID is similar except for the URL it has. DID Document typically contain cryptographic items that enables authentication of the user.
- Decentralized systems: DIDs ingrained in the decentralized systems provide the procedures and features required for DPKI. Development of standards and technologies developed by the community support a lot of blockchains and ledgers.
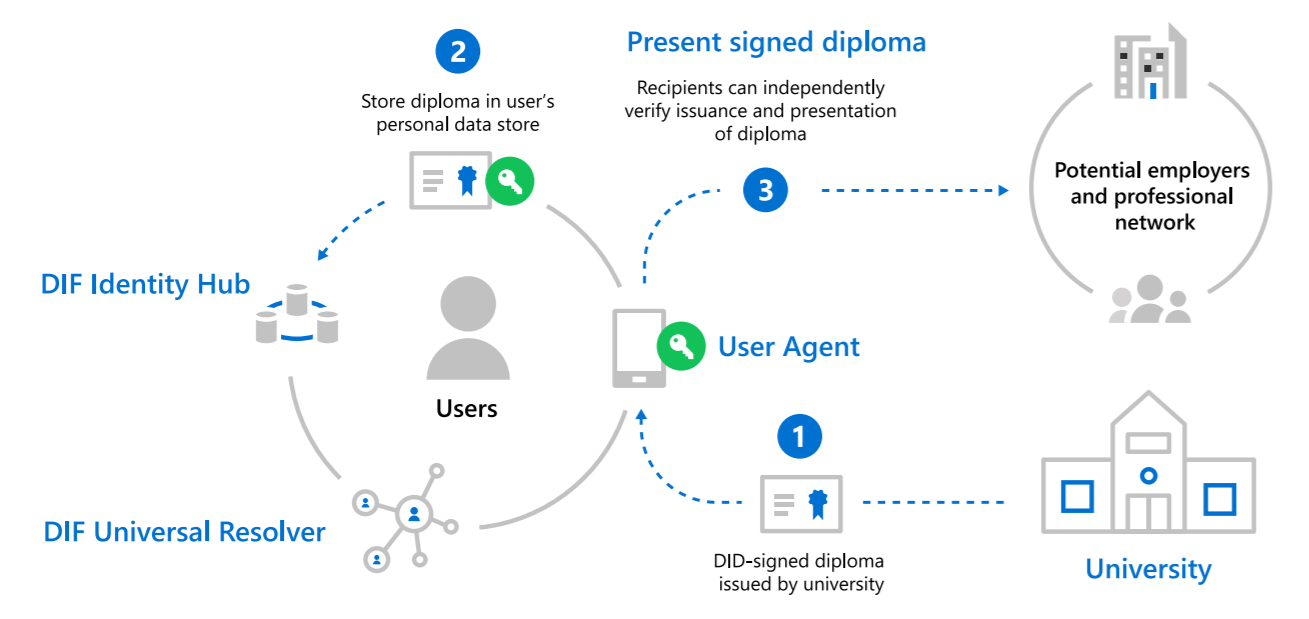
- DID User Agents: The user agent apps assists in creating DIDs. They manage data permissions, and sign or validate DIDs. A Wallet-like app stores the associated data and manages DIDs. These applications enable genuine people to use decentralized identities.
- DIF Universal Resolver: This server uses collection of DID drivers, to provide a standard search and resolution across the implemented decentralized systems. When searched it returns DID Document Object -DDO that summarizes the DPKI metadata associated with that DID.
- DIF Identity Hubs: They facilitate identity data storage and interactions through a replicated network of encrypted personal datastores.
- DID Attestations: Storing the decentralized identities in standard formats helps in processing. It enables identity owners to generate, process, and verify the claims creating the base of trust between users of these systems.
- Decentralized apps and services: DIDs when paired with the Identity Hub, personal datastores helps in creating new class of applications or services. They store data with the user’s Identity Hub and function in the boundaries of permissions granted by the owner.
Access services using the decentralized identity:
An individual creates a pair of private and public keys in an identity wallet. The public key identifier is stored as it is in an ITF. A trusted third party approves the user identity and certifies it with signature of the privately owned key. This certification record is stored in the ITF. The user can access service using this identification by just using QR code or a token. The hash values of identifiers crosscheck their corresponding hash records in the ITF for verification and grant access if they match.
Building decentralized apps and services requires synchronization and replication of data, access to data, managing permissions, and interactions.
Eventually, the people and organizations need to transform their digital identity to the decentralized identity. Things and technology cannot remain same forever, either you update or be ready to be considered outdated.
Take a fresh look, open the door to new opportunities, and let your decentralized identity take care of the rest.
http://www.anarsolutions.com/decentralized-identity/?utm-source=Blogger

No comments:
Post a Comment